Open ports act as security wormholes into mobile devices
Researchers have for the first time characterized a widespread vulnerability in the software that runs on mobile devices.
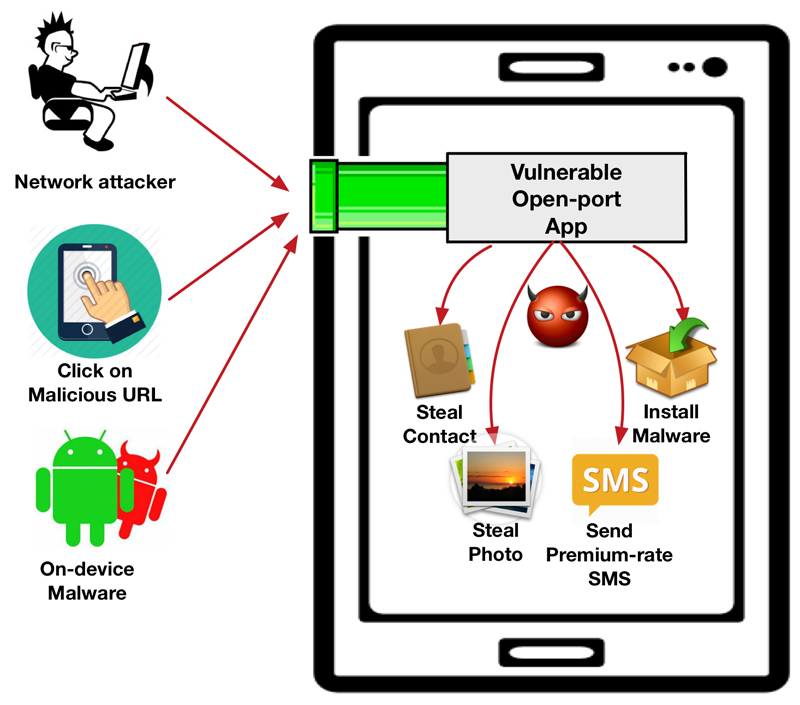
Computer science and engineering researchers at the University of Michigan have for the first time characterized a widespread vulnerability in the software that runs on mobile devices which could allow attackers to steal contact information, security credentials, photos, and other sensitive data, and also to install malware and to perform malicious code execution which could be used in large-scale attacks. The researchers’ findings will be presented at the 2nd IEEE European Symposium on Security and Privacy, which takes place from April 26-28, 2017 in Paris, France.
According to the research team of Yunhan Jack Jia, Qi Alfred Chen, Yikai Lin, Chao Kong, and Prof. Z. Morley Mao, the unguarded use of open Internet ports in application software, which are intended to provide the functionality for computer programs to accept packets from the Internet, can be exploited to create security “wormholes” in mobile devices. Although open ports are routinely used and secured for communications purposes in traditional computing systems, the unique network architecture and usage of mobile systems has led to these vulnerabilities.
The first instance of this type of vulnerability was discovered in November 2015 and was caused by the vulnerable Baidu SDK (software development kit). At least 100 million Android devices were affected.
 Enlarge
Enlarge
The researchers’ paper, “Open Doors for Bob and Mallory: Open Port Usage in Android Apps and Security Implications,” describes their work in performing the first systematic study of open port usage, points to the scale of the vulnerability, and itemizes resultant security implications.
To perform their analysis, the researchers first designed and implemented a tool called OPAnalyzer, which can effectively identify and characterize vulnerable open port usage in Android apps.
Using OPAnalyzer, they performed extensive usage and vulnerability analyses on a dataset with over 100,000 Android applications. OPAnalyzer successfully classified 99% of the mobile usage of open ports into five distinct families, and from the output, the researchers were able to identify several mobile-specific usage scenarios, such as data sharing in physical proximity.
In their subsequent vulnerability analysis, the researchers found that the vulnerable Baidu SDK was only the tip of the iceberg. Nearly half of the usage in the apps studied is unprotected and can be directly exploited remotely. From the identified vulnerable usage, they identified 410 vulnerable applications with 956 potential exploits in total. They manually confirmed the vulnerabilities for 57 applications, including popular mobile apps with 10 to 50 million downloads from official app marketplaces, and also an app that is pre-installed on a series of devices from one manufacturer.
The vulnerabilities in these apps are generally inherited from the various usage of the open port, which exposes the unprotected sensitive functionalities of the apps to anyone from anywhere that can reach the open port. Significantly differing from many previous threats that require malware to be installed on a user’s device to launch attacks, in this threat model an attacker can sit in the LAN, or Internet to send packets, or simply by tricking the user to click an URL on his/her phone.
The paper also investigates the fundamental causes behind this general vulnerability, to see whether it is exposed by popular use cases of open port in the smartphone ecosystem, or just by poor implementation practices. Surprisingly, the researchers found that some usage popular usage scenarios, such as proxy and data sharing within physical proximity are inherently vulnerable to attacks. The authors also categorize the vulnerable open port usages based on their intended usage, and propose mitigation solutions respectively for each category.
The researchers have reported these vulnerabilities to the affected application developers. The Mobile Open Port Security website includes videos of threat model demos, defense demos, and app manufacturer responses.
In one example on the Mobile Open Port Security website, demo [2] shows how a simple click on the URL in a phishing email will trigger the victim’s phone that has one of the vulnerable apps to send a premium-rate SMS.


 MENU
MENU