Security Flaw in New South Wales Puts Thousands of Online Votes at Risk
Securing Internet voting requires solving some of the hardest problems in computer security, and even the smallest mistakes can undermine the integrity of the election result.
 Enlarge
Enlarge
Security researchers Prof. J. Alex Halderman of the University of Michigan and Dr. Vanessa Teague of the University of Melbourne have publicized their discovery of critical flaws in the new Internet voting system designed by the New South Wales, Australia, Electoral Commission and e-voting vendor Scytl.
The iVote system, which its creators describe as private, secure and verifiable, is predicted to see record turnout for online voting in the current election. Voting began on March 16, and by March 21 the iVote system had received more than 66,000 votes. Up to a quarter million voters (about 5% of the total) are expected to use the system by the time voting closes March 28.
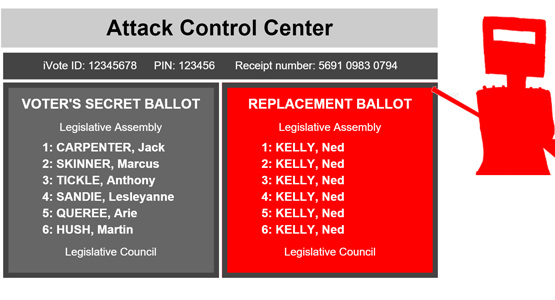
The researchers discovered that while the iVote voting website, cvs.ivote.nsw.gov.au, is served over HTTPS, it included additional JavaScript from an external server, ivote.piwikpro.com. This created a vulnerability for a range of SSL attacks, including the recently discovered FREAK attack.
The researchers confirmed that a man-in-the-middle attacker could exploit the FREAK attack to manipulate a voter’s connection to ivote.piwikpro.com and inject malicious JavaScript into the iVote site without triggering any browser security warnings.
They built a proof of concept that illustrates how this problem could be used by an attacker to steal votes by intercepting and manipulating votes cast to the iVote practise server, though the same attack would also have succeeded against the real voting server. (For legaland ethical reasons, the researchers did not hack the actual election server. They did, however, verify that the real site used the same vulnerable code.)
The researchers reported this vulnerability to CERT Australia at 2 p.m. on Friday, March 20, and around noon the next day the Electoral Commission updated iVote to disable the code from piwikpro.com. Unfortunately, the system had already been operating insecurely for almost a week, exposing tens of thousands of votes to potential manipulation.
According to the researchers, “The vulnerability to the FREAK attack illustrates once again why Internet Voting is hard to do securely. The system has been in development for years, but FREAK was announced only a couple of weeks before the election. Perhaps there wasn’t time to thoroughly retest the iVote system for exposure. We can bet that there are one or more major HTTPS vulnerabilities waiting to be discovered (and perhaps already known to sophisticated attackers). Verification is a vital safeguard against such unknown problems, but at best it detects problems rather than preventing them.”
Securing Internet voting requires solving some of the hardest problems in computer security, and even the smallest mistakes can undermine the integrity of the election result. That’s why most experts agree that Internet voting cannot be adequately secured with current technology.
****
Prof. Halderman is a noted computer security expert whose research places an emphasis on problems that broadly impact society and public policy. He has previously demonstrated security problems with Internet voting sustems in Estonia and in Washington, D.C. His interests include software security, network security, data privacy, anonymity, electronic voting, censorship resistance, digital rights management, computer forensics, ethics, and cybercrime, as well as the interaction of technology with law, governmental regulation, and international affairs. He is the director of the Center for Computer Security and Society.


 MENU
MENU